LXD vs Docker
Miona Aleksic
on 31 March 2022
When talking about containers, a common confusion for potential users of LXD is that LXD is an alternative to Docker or Kubernetes. However, LXD and Docker are not competing container technologies, and they tend to serve completely different purposes. In this blog, we’ll briefly discuss the differences and the suitable use cases for both.

What types of containers are there?
System containers (as run by LXD) are similar to virtual or physical machines. They run a full operating system inside them, you can run any type of workload, and you manage them exactly as you would a virtual or a physical machine. System containers are usually long-lasting and you could host several applications within a single system container. If you’re curious, in What are Linux containers blog, we go a bit deeper into the history of system containers, how they led to LXC, and ultimately, LXD.
Application containers (such as Docker), also known as process containers, are containers that package and run a single process or a service per container. They run stateless types of workloads that are meant to be ephemeral. This means that these containers are temporary, and you can create, delete and replace containers easily as needed.
Both application and system containers share a kernel with the host operating system and utilize it to create isolated processes. The main difference is illustrated below – application containers run a single app/process, whereas system containers run a full operating system giving them flexibility for the workload types they support.
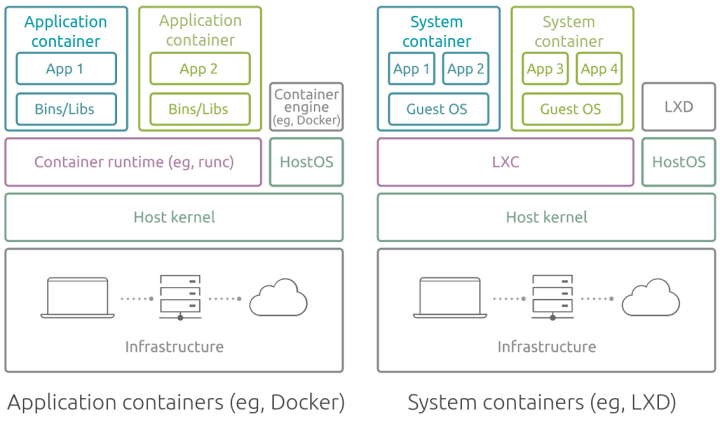
LXD vs Docker
Now that you know the main characteristics of the two container types we can elaborate a bit about LXD vs Docker.
LXD utilises LXC for running system containers. LXC is the technology allowing the segmentation of your system into independent containers, whereas LXD is a daemon running on top of it allowing you to manage and operate these instances in an easy and unified way. When it comes to storage, networking, and logging, LXD supports a variety of interfaces and features that the user can control and interact with. LXD is image-based and you can utilise it to run any kind of workload, including traditional systems you would otherwise run in physical or virtual machines. Overall, functionality-wise, LXD is similar to VMWare or KVM hypervisors, but is much lighter on resources and removes the usual virtualization overhead.
Docker is a containerisation platform, it can be installed on a machine (workstation or a server) and provides a variety of tools for developing and operating containers. One of those tools is containerd – a daemon-based runtime that manages the complete lifecycle of Docker containers, including overall running and monitoring of containers. Docker abstracts away storage, networking, and logging, making it easy for developers that don’t have much prior Linux knowledge. Docker was specifically designed for microservice architecture, providing a way to decompose and isolate individual processes, which can then be scaled independently from the rest of the application or system they are a part of.
For a more detailed comparison, you can visit this blog.
Running Docker in LXD
While LXD and Docker often get compared, they shouldn’t be seen as competing technologies. As illustrated above, they each have their own purpose and place in the digital world. In fact, even running Docker using LXD is possible and suitable in certain circumstances.
You can use LXD to create your virtual systems running inside the containers, segment them as you like, and easily use Docker to get the actual service running inside of the container.
If you are curious about how to do this, please take a look at this tutorial.
Or you can watch the video below, where Stéphane Graber leads you through the process.
You can also visit this blog to learn how to run Docker on Windows and Mac with Multipass.
Further Reading
Learn more about Canonical’s open source infrastructure solutions.
Fast, dense, and secure container and VM management at any scale
LXD brings flexible resource limits, advanced snapshot and networking support, and better security — all making for easier, leaner and more robust containerised solutions and VMs.
